
- What is a VPN?
- Features
-
- Download VPN
-
-
Desktop
- Windows VPN
- macOS VPN
- Linux VPN
-
Mobile
- Android VPN
- iOS VPN
-
Browser Extensions
- Chrome Extension
- Firefox Extension
- Edge Extension
-
-
- Pricing
- Support
- VPN News
VPN vs Proxy vs Tor Explained: Understanding the Differences
The tools people use to protect their privacy online are often discussed together, but they are rarely explained clearly. VPNs, proxies, and Tor are frequently mentioned as interchangeable solutions, even though they work in very different ways and provide very different levels of privacy, security, and anonymity. This confusion can lead users to rely on tools that do not actually protect them in the ways they expect.
As online tracking, data collection, and surveillance continue to grow, understanding how these technologies differ has become increasingly important. This article breaks down what VPNs, proxies, and Tor are, how each one works, and when they are appropriate to use. By understanding the strengths and limitations of each option, readers can make informed decisions about protecting their data and choosing the right tool for their online needs.
Why This Comparison Matters
As online tracking, data collection, and cyber threats continue to increase, more people are looking for tools that offer greater privacy and control. VPNs, proxies, and Tor are often mentioned together, but they serve different purposes and offer very different levels of protection.
Understanding the differences between these technologies is essential for making informed decisions. Choosing the wrong tool can provide a false sense of security, while choosing the right one can meaningfully reduce online risk depending on how and why you use the internet.
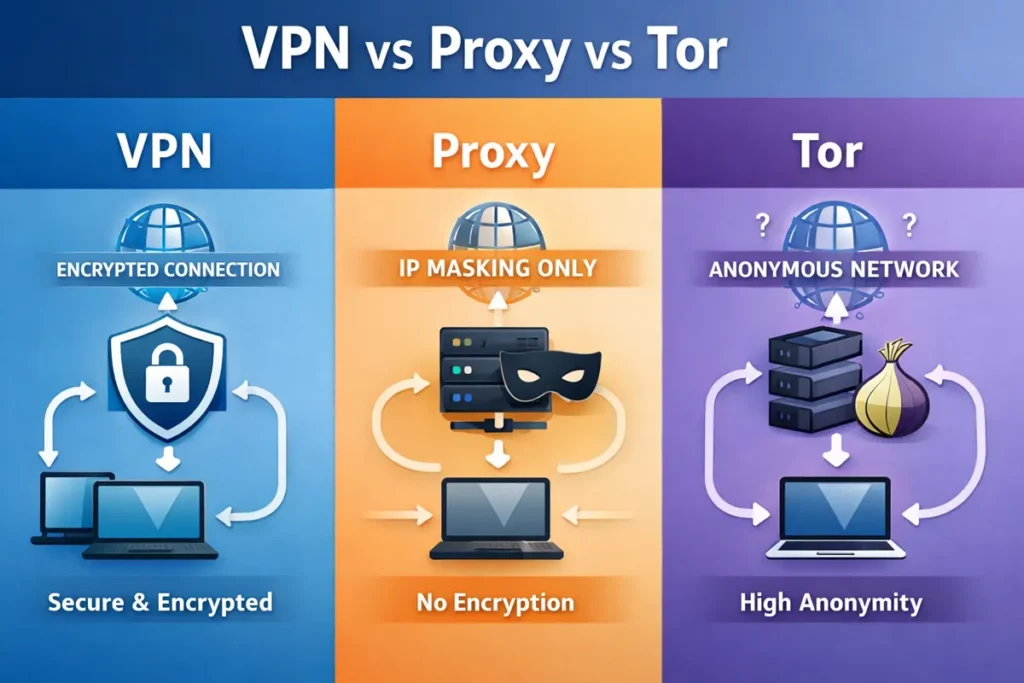
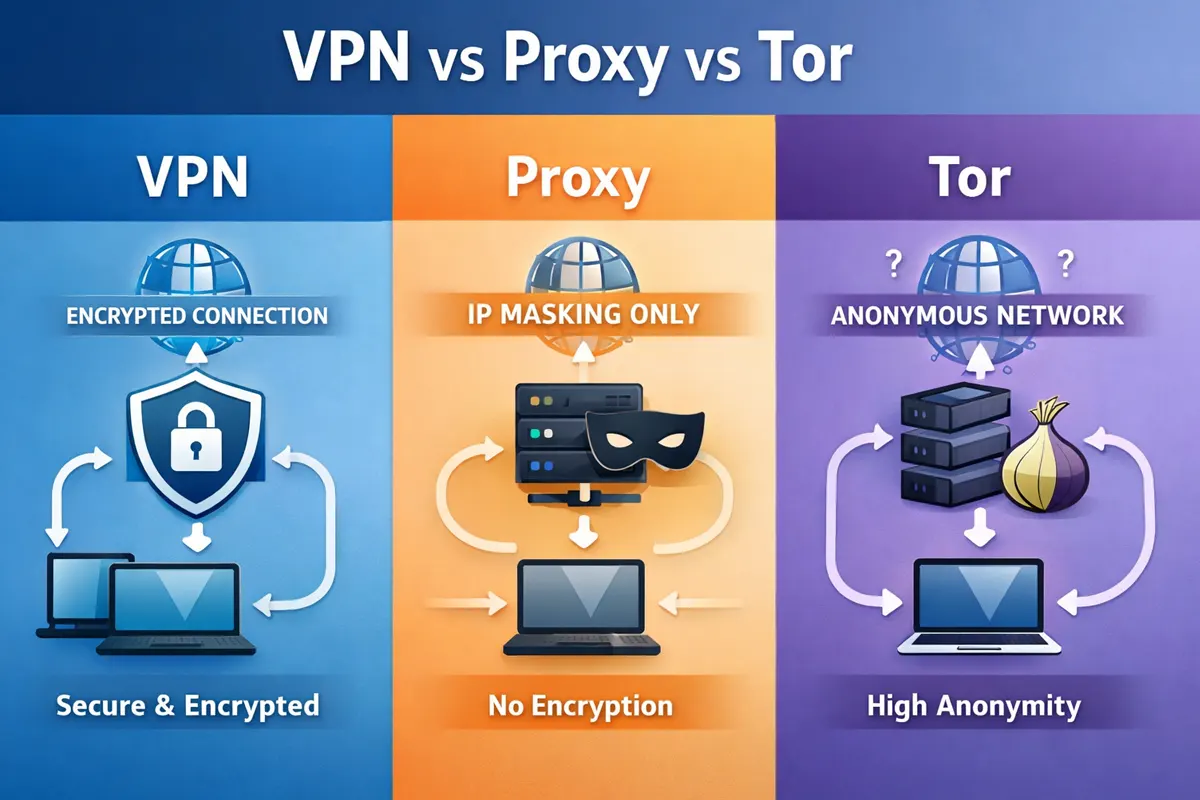
What Is a VPN?
A Virtual Private Network, or VPN, encrypts your internet traffic and routes it through a secure server before it reaches the open internet. This process helps protect data in transit and masks your IP address from websites and networks.
According to the Electronic Frontier Foundation, VPNs are commonly used to protect network traffic from local monitoring and to improve privacy on untrusted connections.
VPNs are widely used by everyday users for secure browsing, public Wi-Fi protection, and reducing exposure to network level tracking.
What Is a Proxy?
A proxy server acts as an intermediary between your device and the internet. When you use a proxy, your request is sent to the proxy server, which then forwards it to the destination website.
Unlike a VPN, most proxies do not encrypt traffic. They typically only route traffic for specific applications or browsers rather than securing all internet activity. Proxies may hide your IP address from websites, but they do not protect data from being observed by networks or internet providers.
Security researchers often caution that proxies provide limited privacy and should not be relied on for sensitive activities.
What is Tor?
Tor, short for The Onion Router, is a network designed to provide strong anonymity by routing traffic through multiple volunteer operated servers. Each step in the process removes identifying information, making it difficult to trace traffic back to the original user.
The Tor Project is widely studied and discussed in academic research and privacy advocacy. Tor is particularly effective at resisting surveillance and censorship, but it comes with tradeoffs such as slower speeds and limited compatibility with some websites.
Tor is best suited for users with high anonymity needs rather than general everyday browsing.
Key Differences Between VPNs, Proxies, and Tor
The most important differences involve encryption, scope of protection, and trust models.
VPNs encrypt all traffic and protect the entire connection
Proxies reroute traffic but usually do not encrypt it
Tor provides strong anonymity through multiple routing layers
The National Institute of Standards and Technology explains that encryption is a critical factor in protecting data confidentiality while it is in transit across networks.
Without encryption, rerouted traffic can still be monitored or intercepted.
Real World Use Cases Compared
VPNs are commonly used for public Wi-Fi protection, remote work, travel, and everyday browsing. They balance privacy, security, and performance in a way that fits most users.
Proxies are often used for simple IP masking or content testing but are not suitable for protecting personal data or sensitive communications.
Tor is frequently used by journalists, researchers, and individuals in restrictive environments who need strong anonymity. However, its slower performance makes it impractical for routine internet use.
Privacy, Security, and Trust Considerations
Each tool requires a different trust model. VPN users place trust in the provider to handle data responsibly. Proxy users often rely on services with little transparency. Tor distributes trust across a decentralized network, reducing reliance on any single operator.
The Cybersecurity and Infrastructure Security Agency consistently emphasizes encryption and secure connections as essential cybersecurity practices.
Understanding these trust differences is critical when choosing a privacy tool.
Choosing the Right Tool for Your Needs
No single option is best for every situation. For most users, a VPN provides the best balance of privacy, usability, and protection. Proxies may be sufficient for limited, low risk tasks. Tor is appropriate for high risk environments where anonymity is critical.
VPN Lightning is designed for users who want practical, privacy focused protection without sacrificing usability, offering encrypted connections built for modern internet use rather than niche scenarios.
Conclusion: Making Informed Privacy Choices Online
VPNs, proxies, and Tor all serve different roles in the privacy ecosystem. While they are often grouped together, they are not interchangeable. Understanding how each works helps users avoid misunderstandings and make better decisions about online safety.
For everyday internet use, tools that encrypt traffic and reduce unnecessary exposure provide meaningful protection. Making informed choices about privacy technology is an essential step toward safer, more confident internet use in an increasingly connected world.
About the Author
J.W. Law is a technology researcher and writer with the VPN Lightning Research Team, specializing in cybersecurity, digital privacy, and consumer internet safety. Their work focuses on translating complex technical and policy topics into clear, practical guidance that helps everyday users better understand how the internet works and how to protect themselves online.
Drawing on research from established organizations, J.W. Law produces evidence-based articles that emphasize accuracy, transparency, and informed decision-making. Their writing is designed to support readers who want reliable, non-sensational information about online security, privacy risks, and modern internet use.
Recent VPN News


Online Privacy Tips for Freelancers and Small Businesses

VPN vs Proxy vs Tor Explained: Understanding the Differences

Can Your Internet Provider See What You Do Online?
ABOUT THE ARTICLE
Frequently Asked Questions
Can my ISP see my browsing history?
Internet providers can typically see the websites your device connects to through domain names and metadata, even if they cannot read the actual content of encrypted pages. Over time, this information can reveal patterns about browsing behavior, interests, and usage habits.
Does private or incognito mode hide activity from my ISP?
No. Private or incognito mode only prevents your browser from saving local history, cookies, and form data on your device. It does not affect how traffic travels across networks or what your internet provider can observe.
What information does HTTPS protect?
HTTPS encrypts the content exchanged between your browser and a website, such as messages, passwords, and page content. However, it does not fully hide metadata like destination domains, connection timing, or data volume, which may still be visible to network operators.
Can ISPs track activity across different devices?
Yes. When multiple devices connect through the same home network or account, providers may associate activity patterns with that connection. This does not mean they can identify individual users, but it can link usage to a household or account.
How does a VPN change what my ISP can see?
A VPN encrypts your internet traffic before it reaches your provider and routes it through a secure server. This prevents ISPs from easily seeing which websites you visit or what DNS requests you make, though they can still see that a VPN connection is being used.
Does using a VPN make me anonymous online?
No. A VPN improves privacy and reduces network visibility, but it does not provide complete anonymity. Websites you log into, browser fingerprinting, and account activity can still identify you unless additional privacy measures are taken.
Why does ISP visibility matter for privacy?
Browsing data and metadata can reveal sensitive information over time, including interests, habits, health research, or financial activity. Reducing unnecessary exposure helps users maintain greater control over their digital lives.
Every Tap. Every Screen. Every Connection. Stay Secure.
VPN Lightning goes beyond standard safeguards. It delivers a unified system for speed, privacy, and digital security. Access lightning-fast routing, select a dedicated IP when necessary, and remain concealed through a strict no-logs commitment. Easy to manage, resilient by design, and created to keep you protected.
- 30-Day Money-Back Guarantee
