
- What is a VPN?
- Features
-
- Download VPN
-
-
Desktop
- Windows VPN
- macOS VPN
- Linux VPN
-
Mobile
- Android VPN
- iOS VPN
-
Browser Extensions
- Chrome Extension
- Firefox Extension
- Edge Extension
-
-
- Pricing
- Support
- VPN News
How Recent VPN Regulations Can Affect Everyone

Virtual Private Networks are no longer niche tools used only by technologists or travelers. They are now part of everyday internet use, helping people protect personal data, secure connections, and maintain privacy online. As VPN adoption has grown, governments and regulators have begun paying closer attention to how these services operate. New and evolving regulations can influence encryption, data handling, and access to secure connections, often in ways that are not immediately obvious to everyday users. Understanding these changes is essential for anyone who relies on the internet to work, communicate, and stay protected online.
Why VPN Regulations Matter Right Now
Virtual Private Networks have moved from niche tools to everyday privacy safeguards. As more people rely on VPNs for secure browsing, remote work, and protection on public Wi-Fi, governments around the world have taken a closer look at how VPNs operate and how they are used.
Recent regulatory changes and enforcement efforts are not limited to a single country or political system. They affect travelers, remote workers, businesses, and ordinary internet users who may not realize that VPN rules can influence privacy, access, and online security. Understanding these regulations is now part of being an informed internet user.
What Governments Are Regulating VPNs
VPN regulations generally focus on a few core areas: data retention, provider transparency, lawful access, and restrictions on encryption or network routing.
According to the Electronic Frontier Foundation, governments often justify VPN regulation under national security or law enforcement frameworks, even though VPNs are widely used for legitimate privacy and safety reasons.
Some regulations require VPN providers to retain user data or register with authorities. Others restrict which VPN services can legally operate within a country or block VPN traffic altogether.
How These Rules Affect Everyday Users
VPN regulations are often discussed in legal or technical terms, but their impact is practical.
When regulations require data logging, user privacy can be reduced. When VPN services are restricted or blocked, people may lose access to tools that protect them on unsecured networks. Travelers may discover that a VPN they rely on at home behaves differently or does not function at all abroad.
The Federal Trade Commission emphasizes that consumers should understand how services handle personal data, especially when laws or policies change how information can be collected or shared.
Encryption and Security Standards Under Scrutiny
Many VPN regulations intersect with broader debates about encryption. Some governments argue for weakened encryption or expanded access to encrypted data, while security experts consistently warn against these approaches.
The National Institute of Standards and Technology has repeatedly affirmed that strong encryption is a foundational requirement for protecting data in transit.
Weakening encryption standards does not only affect criminals. It increases risk for businesses, healthcare systems, journalists, and individuals who rely on secure communication.
For everyday users, the impact of a data breach can extend far beyond the initial incident.
Stolen personal information can be used to open fraudulent accounts, bypass identity verification, or launch targeted phishing attacks. Financial data may be used directly for theft or sold to criminal networks. Even years after a breach, exposed credentials can resurface in new attacks.
The Federal Trade Commission warns that identity theft often begins with data obtained through breaches and advises consumers to act quickly after receiving breach notifications.
Public Wi-Fi, Travel, and Regulatory Reality
Public networks remain one of the most common exposure points for personal data. Regulations that limit VPN availability can unintentionally increase risk for people who depend on VPNs to secure connections in airports, hotels, or shared spaces.
The Cybersecurity and Infrastructure Security Agency continues to advise the use of encrypted connections as a baseline safety measure for internet users.
When VPN access is restricted, users may be left without practical alternatives for protecting their data on untrusted networks.
Global Trends, Not Isolated Events
VPN regulation is not confined to one region. Some countries require provider registration, others impose traffic filtering, and some block VPN protocols at the network level. These policies are evolving and can change quickly.
Academic research has shown that VPN blocking often affects ordinary users more than targeted criminal activity, while also pushing people toward less transparent or less secure tools.
This creates a landscape where understanding local rules and choosing responsible services becomes increasingly important.
Where VPN Lightning Fits Into This Environment
A VPN cannot override laws or eliminate regulatory realities. However, a privacy-focused VPN built around transparency, strong encryption, and clear data handling practices gives users a safer option within existing frameworks.
VPN Lightning is designed with these principles in mind, emphasizing user education, informed choice, and modern security standards rather than secrecy or exaggeration. In a world of shifting regulations, clarity and trust matter more than ever.
Conclusion: Regulation Makes Education Essential
VPN regulations are expanding because VPN use has become mainstream. These rules shape how privacy tools function and who can access them. For everyday users, the most important response is not fear but understanding.
Knowing how VPN regulations affect encryption, privacy, and access helps people make smarter decisions about their online safety. Strong security habits, awareness of local laws, and choosing privacy-first services remain essential.
VPN Lightning supports this informed approach by focusing on education, transparency, and reliable protection for modern internet use. In an increasingly regulated digital world, understanding your tools is part of protecting your freedom online.
About the Author
J.W. Law is a technology researcher and writer with the VPN Lightning Research Team, specializing in cybersecurity, digital privacy, and consumer internet safety. Their work focuses on translating complex technical and policy topics into clear, practical guidance that helps everyday users better understand how the internet works and how to protect themselves online.
Drawing on research from established organizations, J.W. Law produces evidence-based articles that emphasize accuracy, transparency, and informed decision-making. Their writing is designed to support readers who want reliable, non-sensational information about online security, privacy risks, and modern internet use.
Recent VPN News


Online Privacy Tips for Freelancers and Small Businesses

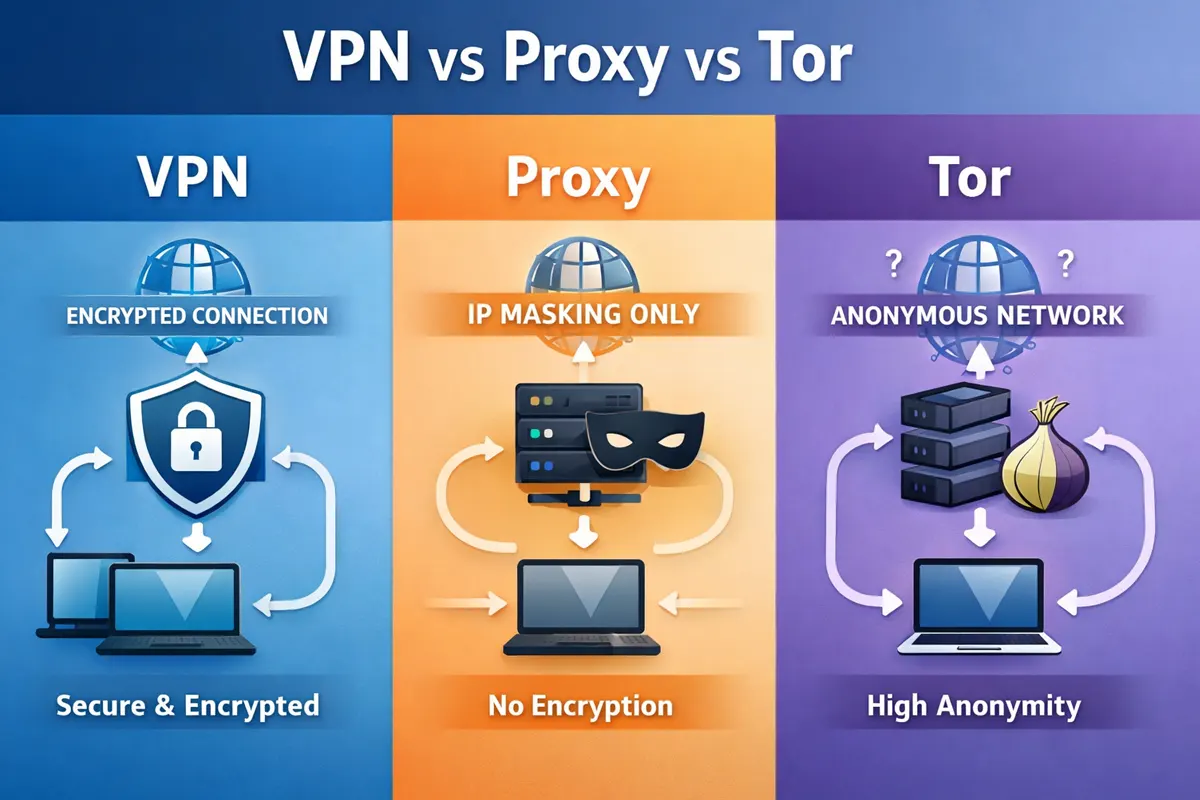
VPN vs Proxy vs Tor Explained: Understanding the Differences

Can Your Internet Provider See What You Do Online?
ABOUT THE ARTICLE
Frequently Asked Questions
Are VPNs legal to use?
In many countries, including the United States, VPNs are legal. Some regions restrict or regulate VPN use, so users should review local laws, especially when traveling.
Why are governments regulating VPNs?
Governments often cite law enforcement, national security, or data oversight concerns. Privacy advocates argue that broad restrictions can harm legitimate users.
Do VPN regulations affect home users?
Yes. Changes to logging rules, encryption standards, or service availability can impact privacy and security even on home networks.
Can a VPN protect me from government surveillance?
A VPN improves privacy and security, but it does not provide immunity from lawful surveillance or override local regulations.
What should users look for in a VPN under new regulations?
Transparency, strong encryption, clear data handling policies, and a commitment to user privacy are key indicators of a trustworthy service.
Each Action. Each Website. Each Visit. Remain Safe.
VPN Lightning provides beyond standard security. It serves as an all-in-one system for performance, confidentiality, and digital safeguarding. Access high-speed routing, select a personal IP if required, and remain private through a verified activity-free policy. Easy to navigate, resilient by design, and engineered to maintain user safety.
- 30-Day Money-Back Guarantee
