
- What is a VPN?
- Features
-
- Download VPN
-
-
Desktop
- Windows VPN
- macOS VPN
- Linux VPN
-
Mobile
- Android VPN
- iOS VPN
-
Browser Extensions
- Chrome Extension
- Firefox Extension
- Edge Extension
-
-
- Pricing
- Support
- VPN News
In this article:
- Why Online Privacy Matters for Small Operations
- Separate Personal and Business Digital Identities
- Secure Internet Connections and Public Wi-Fi Risks
- Protect Client Data and Confidential Information
- Limit Tracking and Data Collection
- Manage Devices, Accounts, and Access
- Build Privacy Into Daily Business Practices
Online Privacy Tips for Freelancers and Small Businesses

Freelancers and small businesses rely on the internet to operate, communicate with clients, manage payments, and store sensitive information. That reliance has grown rapidly as remote work, cloud services, and digital collaboration tools have become standard. At the same time, cyber threats and data collection practices have expanded in ways that disproportionately affect smaller organizations that lack dedicated security teams.
Unlike large enterprises, freelancers and small businesses often blend personal and professional digital lives on the same devices and networks. This creates unique privacy and security risks that are easy to overlook. Understanding how data is exposed online and adopting practical privacy habits is no longer optional. It is a core part of running a sustainable, trustworthy business in a digital first economy.
Why Online Privacy Matters for Small Operations
Freelancers and small businesses are attractive targets because they often hold valuable data without enterprise level protections. Client records, contracts, payment details, login credentials, and intellectual property are frequently stored on personal devices or shared through third party platforms.
According to the Federal Trade Commission, small businesses are increasingly affected by data breaches and cyber incidents, often because basic security practices are missing or inconsistent.
Privacy failures can lead to financial loss, reputational damage, legal liability, and loss of client trust. For independent professionals, even a single incident can have long lasting consequences.
Separate Personal and Business Digital Identities
One of the most common privacy risks for freelancers is blending personal and business activity on the same accounts and devices. Personal email addresses, social media logins, and shared cloud storage can unintentionally expose business data.
The National Institute of Standards and Technology emphasizes the importance of role separation and access control, even for small organizations.
Practical steps include using separate email accounts for business communication, maintaining distinct cloud folders for client work, and avoiding personal app logins on business tools. Clear separation limits damage if one account is compromised.
Secure Internet Connections and Public Wi-Fi Risks
Freelancers often work from cafés, airports, coworking spaces, or client locations. These environments rely on shared networks that may be poorly secured or actively monitored.
The Cybersecurity and Infrastructure Security Agency warns that public Wi-Fi can expose sensitive data to interception if connections are not properly secured.
Using a VPN encrypts internet traffic and reduces exposure on untrusted networks. A privacy first service like VPN Lightning helps protect data in transit without disrupting everyday workflows, especially for mobile or remote professionals.
Protect Client Data and Confidential Information
Many freelancers handle sensitive client information without realizing the legal or ethical responsibility that comes with it. Contracts, personal identifiers, and proprietary data are often shared through email or stored in cloud services.
According to guidance from the Electronic Frontier Foundation, minimizing data exposure and limiting unnecessary data retention are key privacy principles.
Encrypting files, using secure file sharing tools, and deleting data that is no longer needed reduce risk. Privacy is not only about preventing breaches. It is about collecting and keeping less data in the first place.
Limit Tracking and Data Collection
Small businesses are often tracked just as aggressively as large companies, sometimes without realizing it. Advertising trackers, analytics scripts, and third party plugins can collect data about both the business owner and their clients.
Academic research from Princeton University has shown how multiple trackers operate across websites and services, often aggregating data invisibly.
Reviewing website plugins, limiting third party integrations, and using privacy focused browser settings can significantly reduce unnecessary data sharing. A VPN also helps reduce tracking tied to IP addresses and network identifiers.
Manage Devices, Accounts, and Access
Device security is a foundational privacy issue. Laptops and phones used for business should be protected with strong passwords, regular updates, and account level safeguards.
The CISA recommends enabling multi factor authentication, keeping systems updated, and limiting access privileges as basic cybersecurity practices.
For small teams, this means ensuring each person has their own login credentials and removing access promptly when roles change. For solo freelancers, it means protecting the primary email account, which often controls password resets for everything else.
Build Privacy Into Daily Business Practices
Privacy should not be an afterthought or a one time setup. It works best when it becomes part of everyday operations. This includes verifying unusual requests, questioning unexpected links or attachments, and educating clients about secure communication methods.
Security research firms consistently note that many incidents begin with simple social engineering rather than technical exploits. Awareness and routine verification can prevent a wide range of attacks.
Using tools that support encrypted connections and limit passive monitoring, such as VPN Lightning, helps freelancers and small businesses maintain privacy without adding complexity to daily work.
Conclusion: Privacy as a Competitive Advantage
Online privacy is no longer just a technical concern. It is a trust issue. Clients expect their information to be handled responsibly, regardless of business size. Freelancers and small businesses that prioritize privacy reduce risk, protect their reputations, and demonstrate professionalism.
Building strong privacy habits does not require enterprise budgets or advanced expertise. It requires informed choices, consistent practices, and tools that support secure internet use. VPN Lightning is designed for modern professionals who need reliable, privacy first protection that fits naturally into remote and independent work.
In an economy built on digital trust, protecting privacy is not only about defense. It is about long term resilience and confidence in how business is done online.
About the Author
J.W. Law is a technology researcher and writer with the VPN Lightning Research Team, specializing in cybersecurity, digital privacy, and consumer internet safety. Their work focuses on translating complex technical and policy topics into clear, practical guidance that helps everyday users better understand how the internet works and how to protect themselves online.
Drawing on research from established organizations, J.W. Law produces evidence-based articles that emphasize accuracy, transparency, and informed decision-making. Their writing is designed to support readers who want reliable, non-sensational information about online security, privacy risks, and modern internet use.
Recent VPN News


Online Privacy Tips for Freelancers and Small Businesses

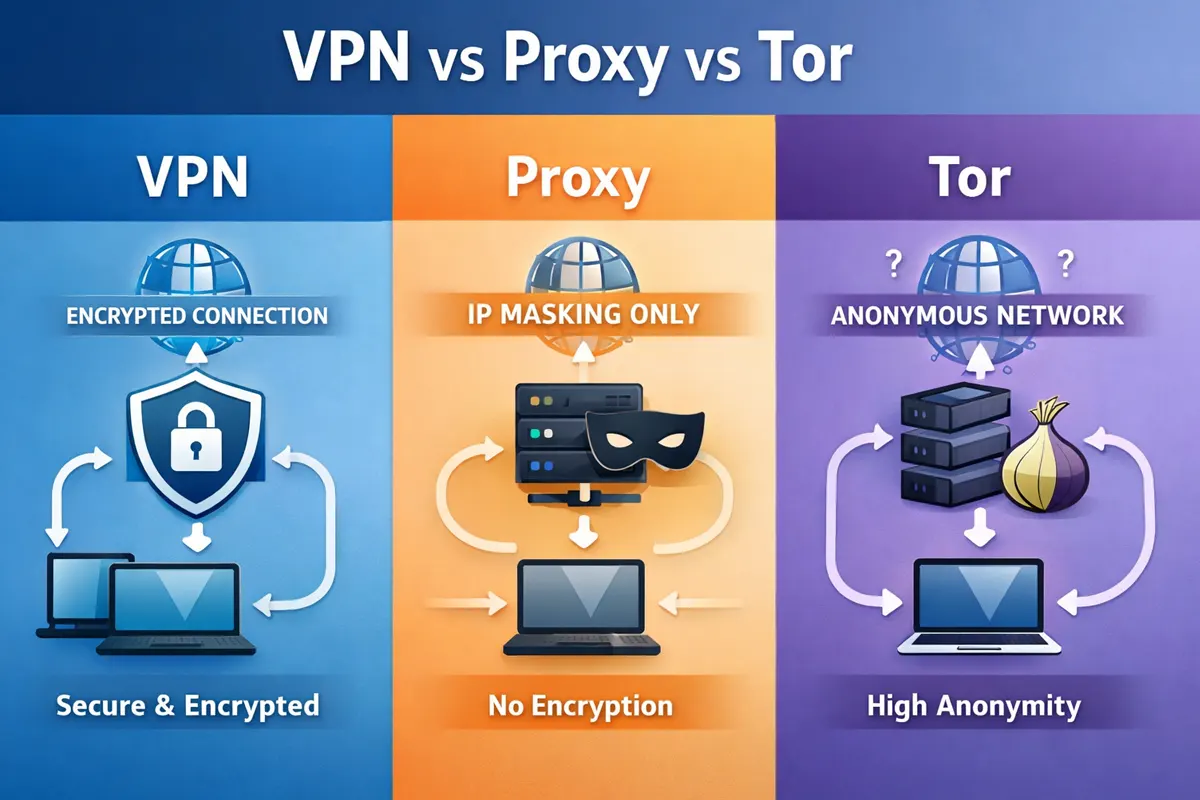
VPN vs Proxy vs Tor Explained: Understanding the Differences

Can Your Internet Provider See What You Do Online?
ABOUT THE ARTICLE
Frequently Asked Questions
Can my ISP see my browsing history?
Internet providers can typically see the websites your device connects to through domain names and metadata, even if they cannot read the actual content of encrypted pages. Over time, this information can reveal patterns about browsing behavior, interests, and usage habits.
Does private or incognito mode hide activity from my ISP?
No. Private or incognito mode only prevents your browser from saving local history, cookies, and form data on your device. It does not affect how traffic travels across networks or what your internet provider can observe.
What information does HTTPS protect?
HTTPS encrypts the content exchanged between your browser and a website, such as messages, passwords, and page content. However, it does not fully hide metadata like destination domains, connection timing, or data volume, which may still be visible to network operators.
Can ISPs track activity across different devices?
Yes. When multiple devices connect through the same home network or account, providers may associate activity patterns with that connection. This does not mean they can identify individual users, but it can link usage to a household or account.
How does a VPN change what my ISP can see?
A VPN encrypts your internet traffic before it reaches your provider and routes it through a secure server. This prevents ISPs from easily seeing which websites you visit or what DNS requests you make, though they can still see that a VPN connection is being used.
Does using a VPN make me anonymous online?
No. A VPN improves privacy and reduces network visibility, but it does not provide complete anonymity. Websites you log into, browser fingerprinting, and account activity can still identify you unless additional privacy measures are taken.
Why does ISP visibility matter for privacy?
Browsing data and metadata can reveal sensitive information over time, including interests, habits, health research, or financial activity. Reducing unnecessary exposure helps users maintain greater control over their digital lives.
Every Tap. Every Screen. Every Connection. Stay Secure.
VPN Lightning goes beyond standard safeguards. It delivers a unified system for speed, privacy, and digital security. Access lightning-fast routing, select a dedicated IP when necessary, and remain concealed through a strict no-logs commitment. Easy to manage, resilient by design, and created to keep you protected.
- 30-Day Money-Back Guarantee
