
- What is a VPN?
- Features
-
- Download VPN
-
-
Desktop
- Windows VPN
- macOS VPN
- Linux VPN
-
Mobile
- Android VPN
- iOS VPN
-
Browser Extensions
- Chrome Extension
- Firefox Extension
- Edge Extension
-
-
- Pricing
- Support
- VPN News
In this article:
Can Your Internet Provider See What You Do Online?

Your internet connection is more than a utility. It is a gateway through which personal data, private communications, and everyday activity constantly flow. Because internet service providers sit at the center of this connection, they occupy a unique position of visibility that many users rarely consider. As privacy concerns grow and data practices face increased scrutiny, understanding what providers can observe and how that information is handled has become a key part of modern digital awareness.
Why Internet Visibility Matters
Every time you open a website, stream a video, or search for information, your internet connection passes through your internet service provider. As privacy concerns grow and internet usage becomes more central to daily life, many people are asking a simple but important question: can your internet provider actually see what you do online?
The answer is nuanced. While modern encryption has improved privacy significantly, internet providers still retain visibility into certain aspects of user activity. Understanding what is visible, what is protected, and where gaps remain is essential for making informed decisions about online privacy and security.
What Internet Providers Can See by Default
Internet service providers manage the networks that connect homes and devices to the broader internet. As a result, they can observe some metadata associated with internet traffic.
According to technical explanations published by Cloudflare, internet providers can typically see destination domains, connection times, and data volumes, even when content itself is encrypted.
This means your provider may not see the exact content of a secure webpage, but it can still know which websites your device communicates with and when.
What HTTPS Protects and What It Does Not
Most websites today use HTTPS, which encrypts the content exchanged between your browser and a website. This prevents intermediaries from reading page contents, messages, or form data.
However, HTTPS does not fully conceal metadata. Security researchers have long noted that domain names and traffic patterns remain visible to network operators.
This distinction is important. Encryption protects content, but it does not fully obscure browsing behavior.
DNS Requests and ISP Visibility
One of the clearest points of visibility for internet providers is Domain Name System traffic. DNS requests translate website names into IP addresses, allowing devices to connect.
Research pubvlished by Princeton University has shown that DNS data alone can reveal detailed browsing habits and behavioral patterns.
Unless DNS requests are encrypted or routed through alternative systems, they are often handled directly by the internet provider.
Data Retention and Policy Considerations
What providers do with this information depends on local laws, company policies, and regulatory frameworks.
In the United States, ISPs are subject to a mix of federal and state regulations, but privacy protections are more limited than many consumers realize. Reporting by the Brookings Institution has highlighted how broadband providers occupy a unique position of insight into user activity compared to individual websites.
This has fueled ongoing debates around data retention, consent, and transparency.
How VPNs Change What ISPs Can See
A VPN encrypts traffic before it reaches the internet provider and routes it through a secure server. As a result, the provider sees an encrypted connection to a VPN server rather than direct connections to individual websites.
Network analysis explanations from the Internet Society confirm that VPNs significantly reduce ISP visibility into browsing destinations and DNS activity.
While providers can still see that a VPN is being used and how much data is transmitted, the specific websites visited are no longer easily observable.
Why This Matters for Everyday Users
ISP visibility is not just a technical issue. It has real implications for privacy, profiling, and security.
Browsing history can reveal sensitive information about health, finances, political interests, or personal circumstances. Even when content is encrypted, metadata can paint a detailed picture over time.
Using tools that reduce unnecessary exposure helps users maintain greater control over their digital lives.
Where VPN Lightning Fits In
A VPN cannot make someone invisible online, nor does it replace good security habits. However, a privacy-focused VPN helps limit how much information flows through internet providers by encrypting traffic and reducing metadata exposure.
VPN Lightning is built with this practical goal in mind, offering encrypted connections and clear privacy practices designed to support everyday users without relying on exaggerated promises.
Conclusion: Understanding ISP Visibility Is Part of Digital Literacy
Internet providers play a central role in how data moves online, which gives them inherent visibility into network activity. While encryption has improved privacy, it has not eliminated all forms of observation.
Understanding what ISPs can see, how that data may be used, and how tools like VPNs affect visibility allows people to make informed decisions about their online security. In an internet shaped by data collection and evolving policies, knowledge remains one of the strongest forms of protection.
About the Author
J.W. Law is a technology researcher and writer with the VPN Lightning Research Team, specializing in cybersecurity, digital privacy, and consumer internet safety. Their work focuses on translating complex technical and policy topics into clear, practical guidance that helps everyday users better understand how the internet works and how to protect themselves online.
Drawing on research from established organizations, J.W. Law produces evidence-based articles that emphasize accuracy, transparency, and informed decision-making. Their writing is designed to support readers who want reliable, non-sensational information about online security, privacy risks, and modern internet use.
Recent VPN News


Online Privacy Tips for Freelancers and Small Businesses

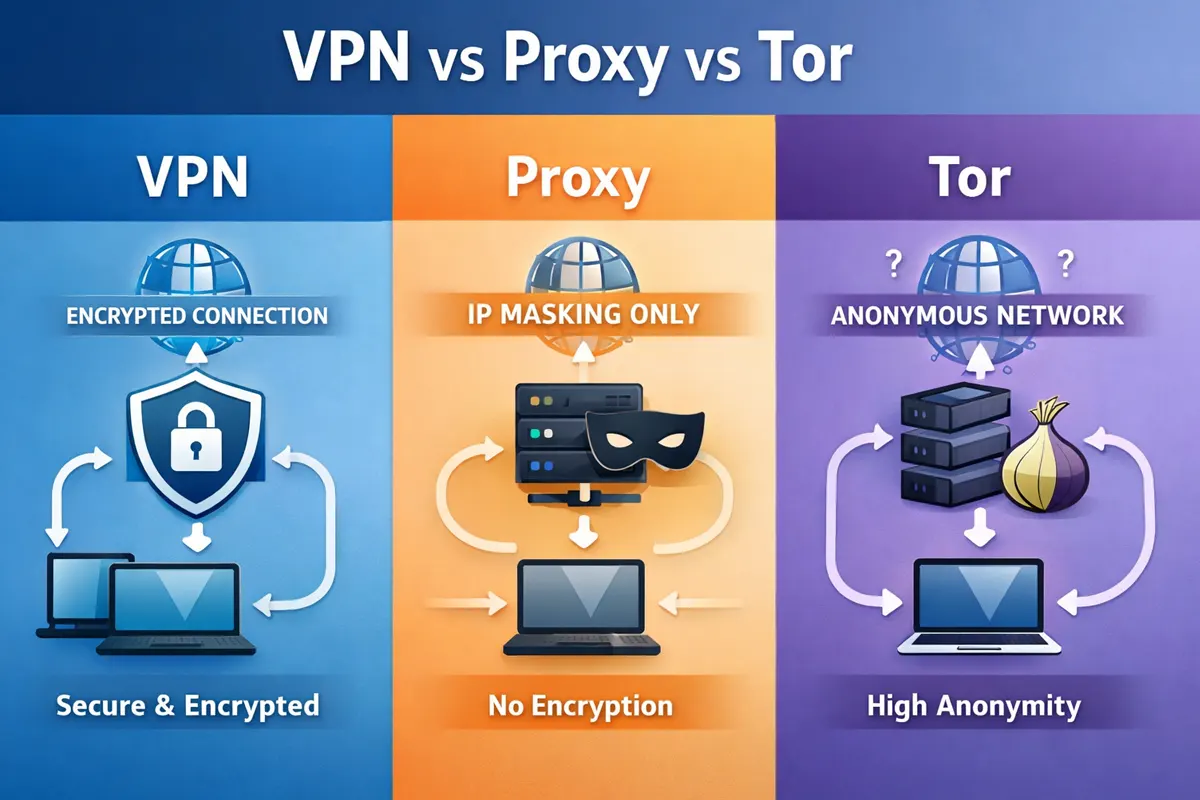
VPN vs Proxy vs Tor Explained: Understanding the Differences

Can Your Internet Provider See What You Do Online?
ABOUT THE ARTICLE
Frequently Asked Questions
Can my ISP see my browsing history?
Internet providers can typically see the websites your device connects to through domain names and metadata, even if they cannot read the actual content of encrypted pages. Over time, this information can reveal patterns about browsing behavior, interests, and usage habits.
Does private or incognito mode hide activity from my ISP?
No. Private or incognito mode only prevents your browser from saving local history, cookies, and form data on your device. It does not affect how traffic travels across networks or what your internet provider can observe.
What information does HTTPS protect?
HTTPS encrypts the content exchanged between your browser and a website, such as messages, passwords, and page content. However, it does not fully hide metadata like destination domains, connection timing, or data volume, which may still be visible to network operators.
Can ISPs track activity across different devices?
Yes. When multiple devices connect through the same home network or account, providers may associate activity patterns with that connection. This does not mean they can identify individual users, but it can link usage to a household or account.
How does a VPN change what my ISP can see?
A VPN encrypts your internet traffic before it reaches your provider and routes it through a secure server. This prevents ISPs from easily seeing which websites you visit or what DNS requests you make, though they can still see that a VPN connection is being used.
Does using a VPN make me anonymous online?
No. A VPN improves privacy and reduces network visibility, but it does not provide complete anonymity. Websites you log into, browser fingerprinting, and account activity can still identify you unless additional privacy measures are taken.
Why does ISP visibility matter for privacy?
Browsing data and metadata can reveal sensitive information over time, including interests, habits, health research, or financial activity. Reducing unnecessary exposure helps users maintain greater control over their digital lives.
Every Tap. Every Screen. Every Connection. Stay Secure.
VPN Lightning goes beyond standard safeguards. It delivers a unified system for speed, privacy, and digital security. Access lightning-fast routing, select a dedicated IP when necessary, and remain concealed through a strict no-logs commitment. Easy to manage, resilient by design, and created to keep you protected.
- 30-Day Money-Back Guarantee
