- What is a VPN?
- Features
-
- Download VPN
-
-
Desktop
- Windows VPN
- macOS VPN
- Linux VPN
-
Mobile
- Android VPN
- iOS VPN
-
Browser Extensions
- Chrome Extension
- Firefox Extension
- Edge Extension
-
-
- Pricing
- Support
- VPN News
VPN News & Information
Stay Informed
Stay Safe
VPN News reflects our belief that everyone deserves a first class internet experience, and that begins with education. This archive delivers clear, reliable reporting on privacy, security, and online technology so readers can make informed decisions online.
Category Filters

What to Do After a Data Breach
A data breach can expose personal information and lead to fraud, identity theft, and account takeover long after the initial incident. This article explains what to do after a data breach, including securing accounts, monitoring financial activity, avoiding follow-up scams, and reducing future exposure. It provides practical, research-based steps for protecting privacy and strengthening online security, helping readers respond confidently and make informed decisions in an increasingly data driven digital world.

Online Privacy Tips for Freelancers and Small Businesses
Freelancers and small businesses depend on the internet to manage clients, payments, and daily operations, yet often lack dedicated security resources. This article explains practical online privacy tips to reduce risk, protect client data, and secure everyday work. It covers separating personal and business accounts, protecting connections on public networks, limiting tracking, and managing devices responsibly. Readers learn why privacy matters, how small teams are targeted, and how informed choices help maintain trust and resilience.

Emerging Cybersecurity Threats to Watch in 2026
Emerging cybersecurity threats are increasingly shaped by identity theft, infostealer malware, and faster ransomware operations, with attackers using automation and AI to scale social engineering. This article explains the risks to watch right now, including credential abuse, cloud account takeover, software supply chain compromise, and extortion focused data theft. It also provides practical steps everyday users can take to reduce exposure.

How Data Brokers Collect and Sell Personal Data
Data brokers quietly collect and trade personal information drawn from online activity, mobile apps, public records, and commercial sources. These companies build detailed profiles that are sold to advertisers, insurers, employers, and other third parties. This article explains how data brokers operate, the types of data they collect, the risks this creates for consumers, and why understanding the data broker economy is essential for protecting privacy.
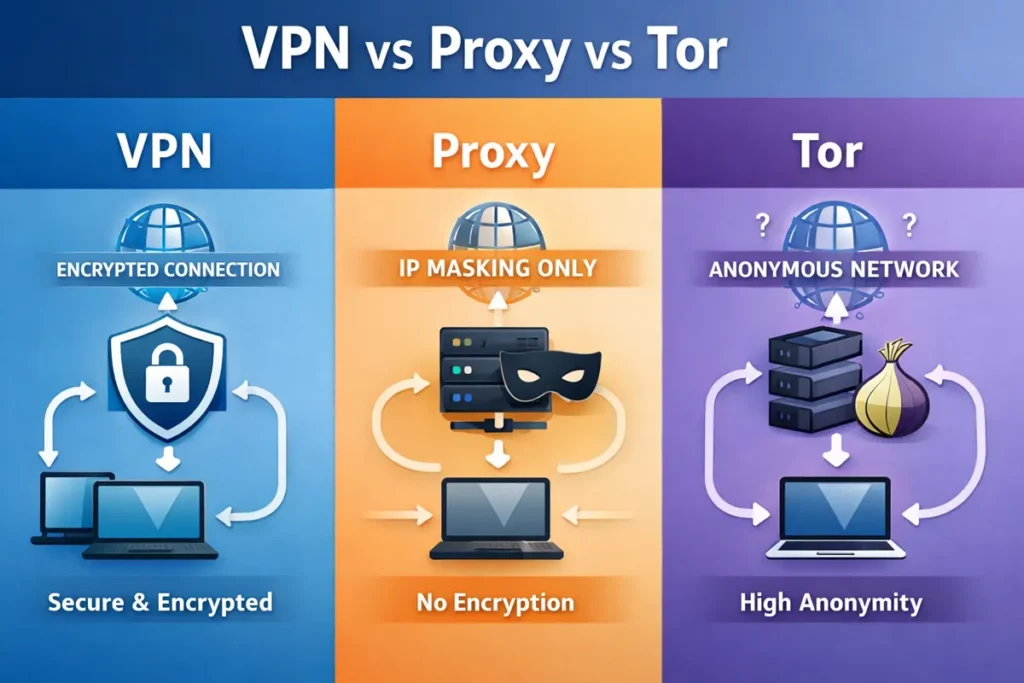
VPN vs Proxy vs Tor Explained: Understanding the Differences
VPNs, proxies, and Tor are often grouped together, but they serve very different purposes online. Each tool handles privacy, security, and anonymity in distinct ways, with important tradeoffs for everyday users. This article explains how VPNs, proxies, and Tor work, where they differ, and when each is appropriate. Understanding these differences helps readers avoid false security assumptions and choose the right privacy tool.

Can Your Internet Provider See What You Do Online?
Internet service providers play a central role in how data moves online, which gives them visibility into certain aspects of user activity. While encryption has improved privacy, it does not eliminate all forms of tracking or metadata exposure. This article explains what ISPs can see, what remains protected, and how tools like VPNs affect visibility, helping readers understand how their online behavior is observed and what steps can reduce unnecessary exposure.

What Is a Free VPN and Do They Keep You Safe?
Free VPN services promise privacy at no cost, but the reality is often more complex. Many free VPNs rely on data collection, advertising, or technical limits that can weaken security and create false confidence. This article explains how free VPNs operate, the risks identified by regulators and researchers, and what everyday users should consider before trusting a no-cost service with their online activity so readers can make informed, realistic choices about privacy and protection online.

How Recent VPN Regulations Can Affect Everyone
As VPN use becomes more common, governments around the world are introducing new regulations that affect how privacy tools operate and who can use them. These changes can influence encryption standards, data handling practices, and access to secure connections, even for everyday users. Understanding how VPN regulations work helps people make informed decisions about their online privacy, security, and freedom in an increasingly regulated digital environment.

Data Breaches in 2025 and What Everyone Should Know
Data breaches have become a routine risk for consumers as companies collect and store more personal information than ever before. From email addresses to financial details, exposed data can lead to identity theft, fraud, and long term privacy harm. This article explains what a data breach is, how breaches happen, why they matter to everyday users, and practical steps individuals can take to reduce risk and respond effectively when personal information is exposed online today.

Why You Should Use a VPN: A Practical Guide to Privacy
Using a VPN helps protect your online activity in a world where data collection, public Wi-Fi risks, and tracking are increasingly common. A virtual private network encrypts your internet traffic, reduces exposure to network monitoring, and adds protection when using shared or unfamiliar connections. This article explains why VPNs matter today, how they support privacy and security, and what everyday users should understand before choosing a VPN service.

What Is a Virtual Private Network and How Does It Work?
A VPN creates an encrypted tunnel between your device and the internet, helping protect data as it travels across networks you do not control. By masking your IP address and securing traffic, a VPN reduces tracking and improves safety on public and private connections. This article breaks down how VPNs work, what they protect, their limits, and why understanding VPN technology matters for modern internet use for everyday users seeking privacy, security, and informed control.
Each Action. Each Site. Each Interaction. Stay Safe.
VPN Lightning provides beyond standard coverage. It functions as an all-in-one system for performance, confidentiality, and digital safety. Access rapid networks, select a dedicated address when required, and remain private through a no-logs policy.
- 30-Day Money-Back Guarantee
